Team Wabbi
October 3, 2023
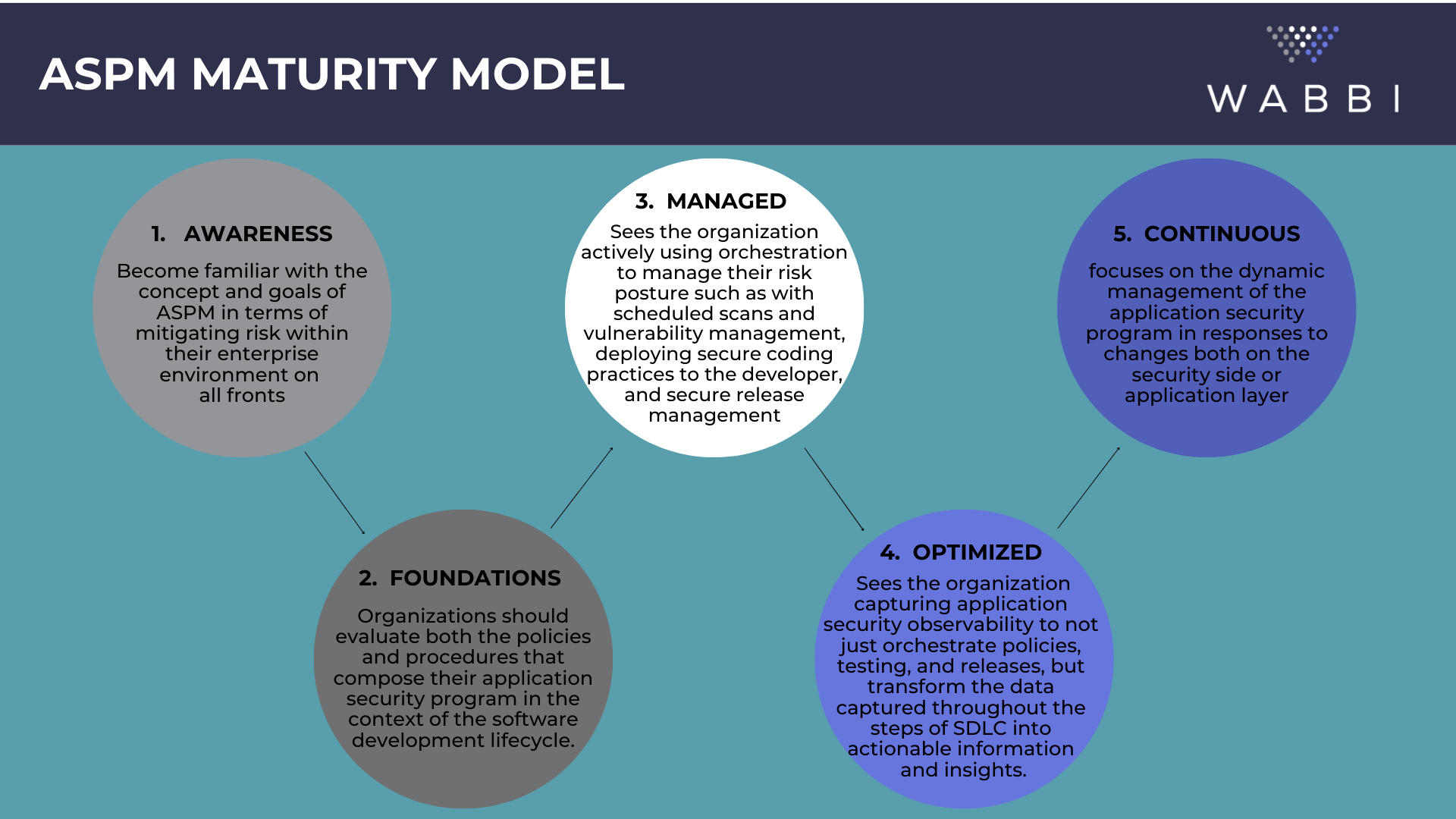
What is Application Security Orchestration & Correlation (ASOC)?
Application Security Orchestration & Correlation is the use of automation to manage components of an application security program in response to a pre-defined workflows to enable integration into the software development lifecycle (SDLC).
- Orchestration involves the automation of processes in coordination with the SDLC such as AST, vulnerability management, configuration testing, and remediation.
- Correlation centralizes and standardizes results to reduce noise and provide a comprehensive view of application security data over time as a single pane of glass.
By combining both orchestration and correlation capabilities into one platform ASOC creates a centralized management system for all components of an organization’s application security program. By automating the application security process, organizations are able to maintain the velocity of development while ensuring secure code.
End-to-End Application Security Program Orchestration
At its core, ASOC is about unifying all components of an application security program. It is a centralized management system that helps organizations manage all components of their application security program. This includes activities such as secure coding practices, vulnerability scanning, penetration testing, and risk analysis. By leveraging automation and orchestration capabilities in the form of workflow automation tools or specialized ASOC platforms, these activities become more efficient. This efficiency translates into increased visibility for developers who can quickly identify and address any security issues impacting their applications faster than ever before. It also provides a single platform for automation that simplifies the implementation of secure coding practices across all development teams.
ASOC takes a holistic view of all processes and procedures of application security program, not just managing testing results, and should include:
- Policy Deployment & Attestation
- Scheduled Testing
- Ticketing Integrations
- Vulnerability Management
- Compliance Reporting
Through ASOC, organizations are able to weave comprehensive application security throughout their entire SDLC in order to ensure that their applications remain secure. This provides them with a clear view of any security activities and tasks for their applications while keeping pace with business goals such as speed-to-market or cost savings initiatives. Furthermore, ASOC allows organizations to reduce manual overhead associated with traditional security processes which can help improve operational efficiencies for Development, Security & Operations teams.

SDLC Integration with Application Security Orchestration & Correlation
Without ASOC, organizations cannot keep pace with modern software development processes, and is therefore critical to enable organizations to automate, scale, and integrate application security processes into the software development lifecycle (SDLC). ASOC provides consistency and accountability in AppSec processes so that Development can be empowered to own the day-to-day execution without disrupting their workflows. This ensures development teams to ensure they maintain velocity while developing more secure code.
ASOC also streamlines application security programs by providing a single source of truth across multiple sources of data-related application security. This helps organizations make better decisions faster by giving them access to the right information at the right time. Additionally, ASOC can be used to detect vulnerabilities in applications at different stages of the SDLC such as during testing or deployment phases. The correlation engine helps organizations prioritize and triage security activities in line with the organization’s policies and procedures and if needed can provide enforcement to ensure missed SLAs don’t slip through. This helps ensure that any discovered issues are addressed before the application is released into production, which can be up to 100x cheaper than after release. Furthermore, ASOC provides organizations with more accurate correlation capabilities by aggregating data from different sources which can then be used to detect patterns or anomalies that may otherwise have gone unnoticed or misunderstood.
Without feedback from the SDLC full orchestration cannot be executed as it will lack awareness as to when to run and enforce these processes. Key areas to ensure integration between application security and DevOps workflows are:
- Code: Project & Feature Level-Policies should be made available on feature tickets or directly in the IDE for Developers with the ability for Developers to attest
- Test: Automatically start scans based on triggers in the SDLC, such as a check-in or release approval
- Test: Push vulnerabilities into ticketing system backlogs based on criticality thresholds (and not push ones that are below thresholds)
- Release: Have release tools check with your ASOC platform to provide go/no-go decision
- Monitor: Integrate with ticketing systems to ensure vulnerabilities are remediated within defined SLAs
Want to learn more about how you can integrate AppSec in your Development pipeline?
Check out these top resources!



Related Articles

December DevSecOps Roundup: Trends Steering the Future of AppSec
Hey! We’re back with the latest in DevSecOps, security by design, and everything in between. Grab your coffee ☕, and let’s dive in! 📌 Top Blogs 🟣 Zero Trust in AppSec: Why It Belongs in Your Pipelines, Too Zero Trust doesn’t end at the firewall. It belongs in your...

How Hackers Use AI Today—And How To Stay Safe – Forbes –
This article originally appeared on Forbes on July 23, 2025 Expert Panel® Forbes Councils Member Forbes Technology Council COUNCIL POST| Membership (Fee-Based) getty As artificial intelligence advances, so do the tactics of malicious actors. Hackers are now...

Policy as Code: The Missing Link in DevSecOps Maturity
Policy as Code: The Missing Link in DevSecOps Maturity For years, the promise of DevSecOps has been clear: integrate security into development without slowing delivery. Organizations have invested heavily in automation, CI/CD pipelines, and vulnerability scanning. But...

Remote Work Cybersecurity Risks (And How To Reduce Them) – Forbes –
This article originally appeared on Forbes on December 15, 2025 Expert Panel® Forbes Councils Member Forbes Technology Council COUNCIL POST| Membership (Fee-Based) getty Remote and hybrid work have opened the door to greater flexibility, stronger talent pipelines and...

How Tech Companies Can Break Out Of Innovation Stagnation – Forbes –
This article originally appeared on Forbes on November 5, 2025 Expert Panel® Forbes Councils Member Forbes Technology Council COUNCIL POST| Membership (Fee-Based) getty For tech companies, early success can be both a gift and a trap. The same products and systems that...