CONTINUOUS SECURITY solutions
Application Security Posture Management (ASPM)
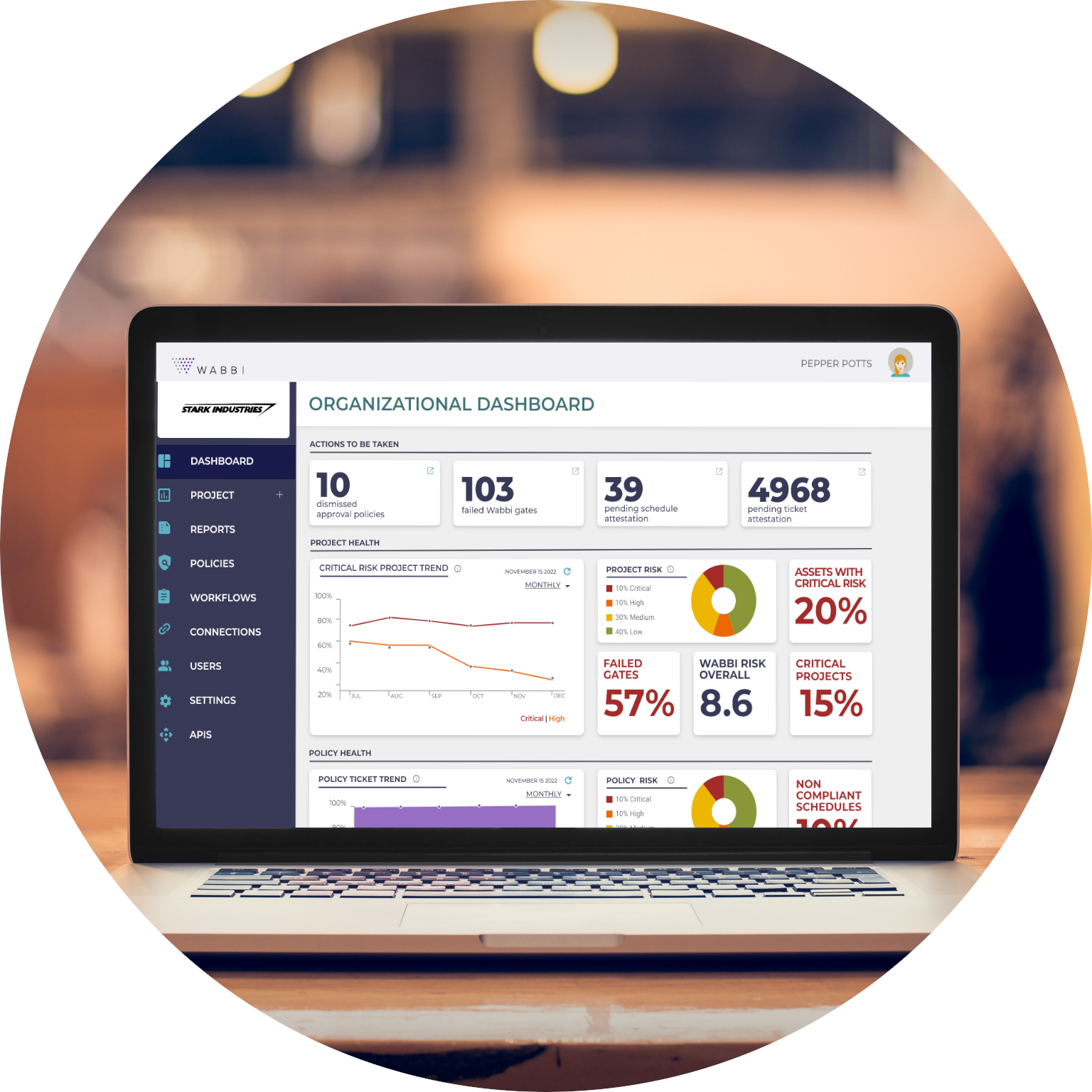
Application Security is so much more than just vulnerabilities
NO-CODE
ORCHESTRATION
Automatically assign security policies based on project attributes and your risk profile for each application, version, environment, and asset. Then, translate those policies into orchestrated workflows from ticket creation to scheduled scans, approvals and controls – all from one platform: Wabbi. ➜
APPLICATION SPECIFIC
CORRELATION
Take release management out of Excel and into the development process. With full visibility into what policies have and haven’t been followed, and what needs to be done to bring an application into compliance, Wabbi is the ultimate go/no-go for security gatekeeping to keep secure code shipping.
CONTEXT-BASED
PRIORITIZATION
Utilize automation and correlation techniques to analyze security data from various sources and enrich it with contextual information relevant to the application being protected. By incorporating contextual insights into the prioritization process, Wabbi enables security teams to focus their efforts on addressing the most significant risks first. ➜
RISK-BASED
MANAGEMENT
Integrate security tools and processes to identify, prioritize, and remediate security risks in real-time. Wabbi enables organizations to adopt a proactive approach to application security by focusing resources on mitigating the most significant risks, thereby reducing the likelihood of security incidents and minimizing their impact on critical assets.
Discover Our ASPM Solutions
Find out how our ASPM program can help you automate security policies, prioritize risks, and ensure continuous compliance.
Risk Management by Design
AUTOMATED & CENTRALIZED
Customize risk requirements by project to prioritize security activities and efforts in the SDLC.
Manage security requirements dynamically in response to changes on the application layer or in security policies.
Scale your application security program without introducing friction or manual efforts no matter how many data sources.