Team Wabbi
July 7, 2023
Now that you understand Application Security Posture Management is the backbone of any application security and DevSecOps program, it’s time to start to build your deployment strategy. Don’t worry – you don’t have to boil the ocean to start to see the hard ROI in 1-3 months (Gartner). With the ASPM Maturity Model, you’ll get the fundamentals to chart your course to finally achieving application security integration into the software development lifecycle (SDLC) and realizing the promise of DevSecOps.
Getting started with ASPM
Getting started with ASPM, although essential, can seem daunting, but with the right knowledge and resources, it is possible to create an effective security posture. Application Security Posture Management (ASPM) is a process that helps organizations identify, assess, and ensure that applications are protected against potential threats by providing comprehensive visibility into the application’s security posture and risk.
When getting started with ASPM, it’s important to understand the key components involved: risk management, vulnerability management, and observability. Risk management is the process of identifying potential vulnerabilities within an application and taking steps to mitigate them. Policy implementation involves setting guidelines for how applications should be built securely for that organization. Finally, observability allows companies to leverage automation to orchestrate and correlate data from application security, DevOps, and DevSecOps tools for actionable insights and dynamic program management. Together, these components allow an enterprise to monitor application security activity and identify any potential risks or threats before they become a bottleneck – or a breach – in the future.
When implementing a successful ASPM strategy within an enterprise environment it is important to consider how all components interact with one another to ensure proper coverage across all applications being monitored as well as limit false positives when reporting on vulnerabilities found during scans. To this end, it is also critical that proper communication between teams exists so that when issues arise they can be efficiently addressed while still maintaining a secure posture at all times. Enterprises should set up processes for continuous monitoring of their systems; this includes both manual checks by personnel as well as automated scans or controls using dedicated tools.
By taking these steps you will be able to maintain a secure posture throughout your organization while still allowing for secure software development lifecycles without making a tradeoff between velocity or security.
ASPM Maturity Model
Developing an Application Security Posture Management (ASPM) roadmap is a crucial step in the implementation process, as it will provide a clear path forward toward achieving the desired security posture. This roadmap should include all components of the ASPM system, including risk assessment vulnerability management, and observability, as well as the broader ecosystem of security and development tools necessary to implement the policies, procedures, and controls. By evaluating it in the context of a maturity model, it allows organizations to quickly capture the benefits of small use cases – such as secrets management – to set the stage for a scalable DevSecOps program built around a core of continuous improvement.
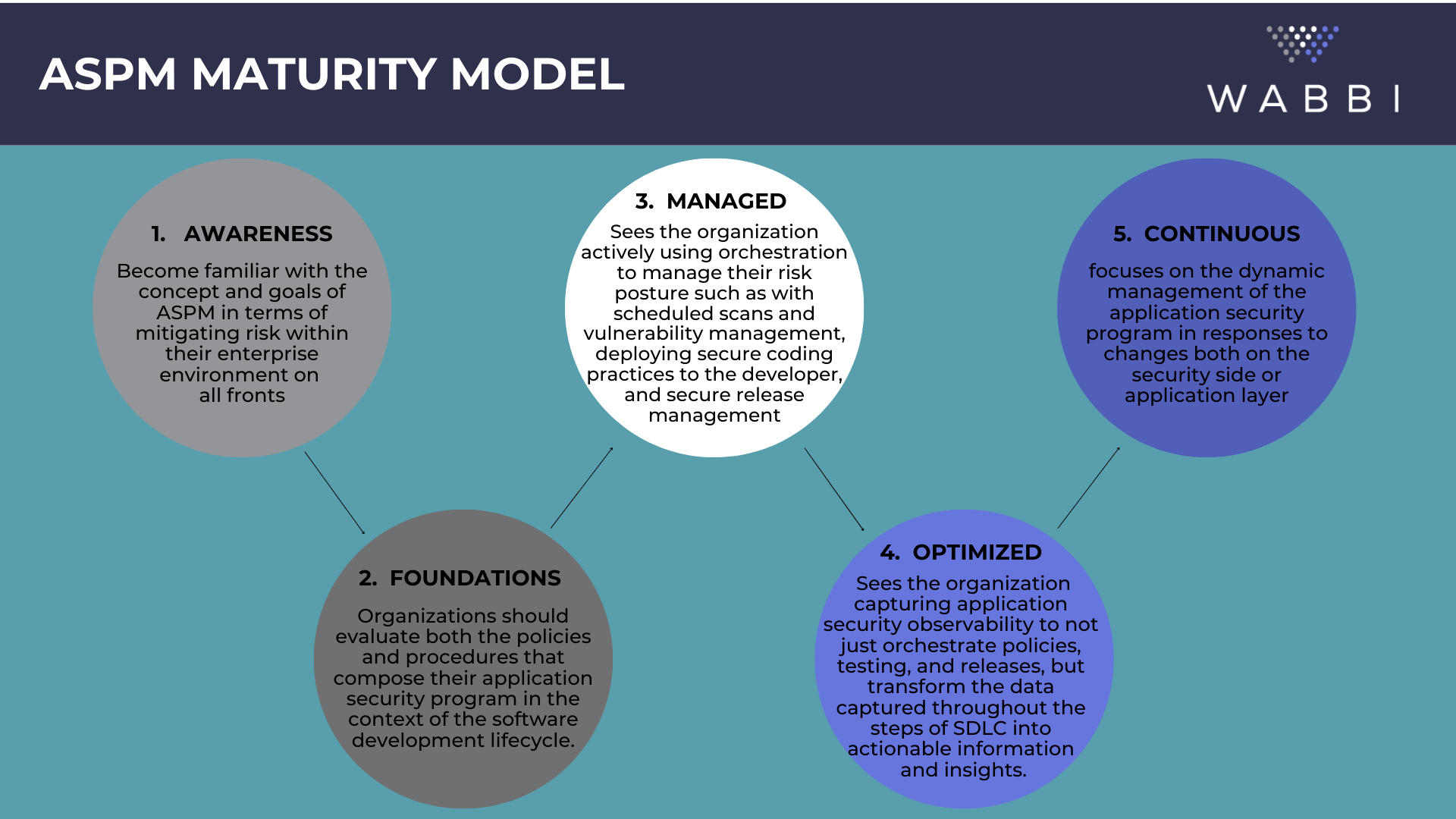
The first stage is ‘Awareness’, organizations should become familiar with the concept and goals of ASPM in terms of mitigating risk within their enterprise environment on all fronts. Education at this stage includes the understanding that integrated security doesn’t just reduce breach risk, but also project delivery risk. It also ensures organizations understand that secure code is not locked up code, but code that has been developed in accordance with security policies that align with an organization’s overall risk profile. This Awareness phase is critical to setting the foundation for breaking down the silos between Dev, Sec, & Ops that have plagued Application Security and DevSecOps initiatives.
The second stage is ‘Foundations’ where the organization should evaluate both the policies and procedures that compose their application security program in the context of the software development lifecycle. Additionally, use cases should be defined as part of the implementation timeline as it’s not expected to implement a full ASPM program overnight. By starting small and giving each use case its own roadmap, enterprises can capture the benefits of implementing basic application security policies (even with manual attestations), regular vulnerability scans, and risk-mitigating controls quickly.
The third stage is ‘Managed’, which sees the organization actively using orchestration to manage their risk posture such as with scheduled scans and vulnerability management, deploying secure coding practices to the developer, and secure release management. A fundamental technology underpinning here is the use of application security orchestration and correlation (ASOC) to enable scalability of AppSec teams and consistency in compliance with the program. This stage enables the shift of ownership of the day-to-day management of Application Security to the Development teams as part of their existing workflows, without sacrificing accountability or agility.
The fourth stage is ‘Optimized’ which sees the organization capturing application security observability to not just orchestrate policies, testing, and releases, but transform the data captured throughout the steps of SDLC into actionable information and insights. At this stage, the technology allows the focus to shift from implementation to improvement. And automation and orchestration aren’t just used for compliance, but also communication between the teams.
Finally, the fifth stage is ‘Continuous’ which focuses on the dynamic management of the application security program in responses to changes both on the security side or application layer. These changes could be known or unknown and keep focus on code always shipping in line with the most current security standards no matter how fast Development, Operations and Security teams are moving. With the Continuous Security stage, organizations ensure comprehensive coverage of their application security posture while minimizing risk exposure.
By leveraging this maturity model when developing an ASPM roadmap, organizations can ensure comprehensive coverage of their security posture while minimizing risk exposure at every stage of implementation. Following these steps carefully will help organizations achieve success when implementing ASPM systems across their enterprise landscape to finally realize the promise of fully integrated security in the SDLC.
Ready to learn more?
Watch our ASPM 102 Wabbinar:
The ASPM Maturity Model
Or check out these resources:
Related Articles

The Cultural Shift Driving Dev Sec Ops Success
The Cultural Shift Driving Dev Sec Ops Success For years, security has been seen as the final step before deployment—a gatekeeper rather than an enabler. But as the software development lifecycle has evolved, so too has the need to integrate security into every phase...
Bridging Cybersecurity and Innovation
Click below to listen to this episode of Strategy Next, where host Jon Lobb sits down with Brittany Greenfield, founder and CEO of Wabbi, to discuss the critical role of foundational security practices, and how organizations can navigate the balance between innovation...

Balancing Act: Integrating Security Seamlessly into User Experience
Balancing Act: Integrating Security Seamlessly into User Experience In today’s hyper-connected world, users expect seamless digital experiences—fast, intuitive, and secure. Yet for many organizations, the traditional tug-of-war between security and user experience...

DevSecOps in Digital Transformation
Click below to listen to this episode of Digital Shifts aka Corporate Evolution Tales, where host Mariam sits down with Brittany Greenfield, founder and CEO of Wabbi, to discuss how to align security with business goals, and why transformation is a continuous...

Tech Deep Dives: DevSecOps Secrets
Click below to listen to this episode of Kabir's Tech Dives, where host Kabir sits down with Brittany Greenfield, founder and CEO of Wabbi, to discuss how Wabbi is revolutionizing application security, the role of cybersecurity in development, and why modern...
