Team Wabbi
January 12, 2024
What is Continuous Security And Why Is It Important?
Security in the CI/CD Evolution
66.8% of security teams

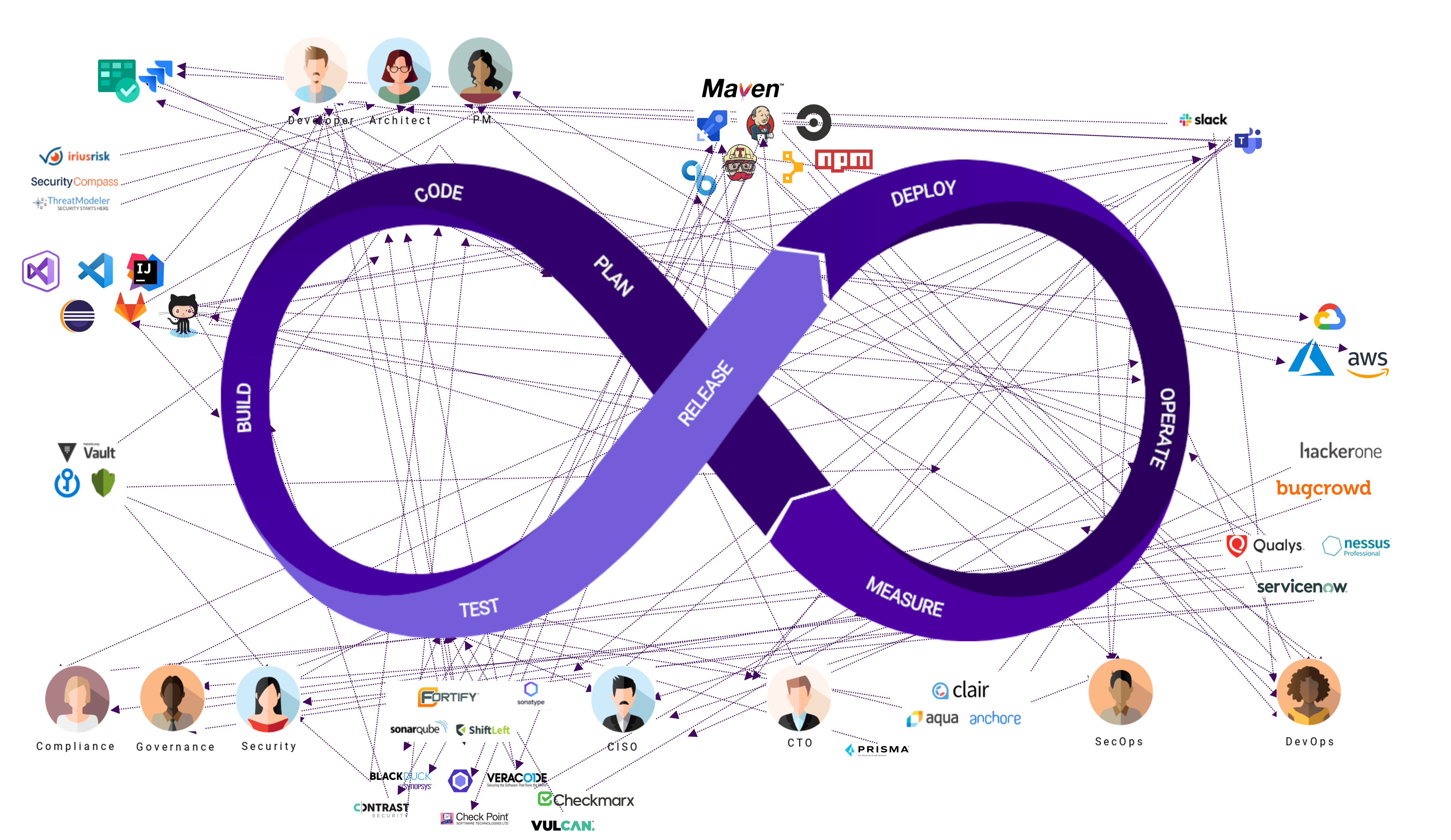
The Continuous Security Ecosystem
The CI/CD/CS
The next step in the CI/CD is to include security at every step of the SDLC.
Automation and Orchestration:
Collaboration… but Segmentation:
Want to learn more about how you can integrate AppSec in your Development pipeline?
Check out these top resources!



Related Articles

December DevSecOps Roundup: Trends Steering the Future of AppSec
Hey! We’re back with the latest in DevSecOps, security by design, and everything in between. Grab your coffee ☕, and let’s dive in! 📌 Top Blogs 🟣 Zero Trust in AppSec: Why It Belongs in Your Pipelines, Too Zero Trust doesn’t end at the firewall. It belongs in your...

How Hackers Use AI Today—And How To Stay Safe – Forbes –
This article originally appeared on Forbes on July 23, 2025 Expert Panel® Forbes Councils Member Forbes Technology Council COUNCIL POST| Membership (Fee-Based) getty As artificial intelligence advances, so do the tactics of malicious actors. Hackers are now...

Policy as Code: The Missing Link in DevSecOps Maturity
Policy as Code: The Missing Link in DevSecOps Maturity For years, the promise of DevSecOps has been clear: integrate security into development without slowing delivery. Organizations have invested heavily in automation, CI/CD pipelines, and vulnerability scanning. But...

Remote Work Cybersecurity Risks (And How To Reduce Them) – Forbes –
This article originally appeared on Forbes on December 15, 2025 Expert Panel® Forbes Councils Member Forbes Technology Council COUNCIL POST| Membership (Fee-Based) getty Remote and hybrid work have opened the door to greater flexibility, stronger talent pipelines and...

How Tech Companies Can Break Out Of Innovation Stagnation – Forbes –
This article originally appeared on Forbes on November 5, 2025 Expert Panel® Forbes Councils Member Forbes Technology Council COUNCIL POST| Membership (Fee-Based) getty For tech companies, early success can be both a gift and a trap. The same products and systems that...