Team Wabbi
January 10, 2024
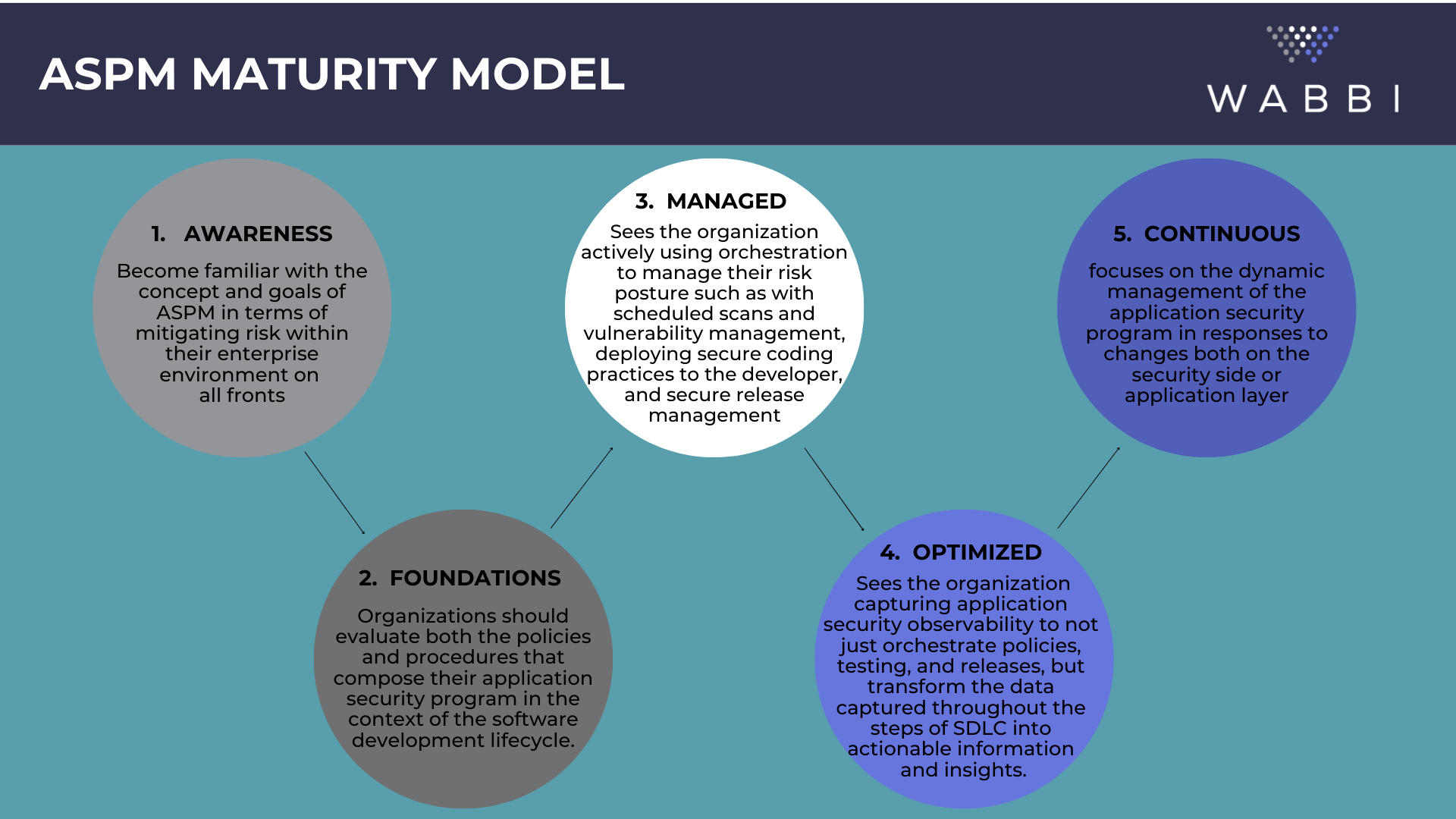
Application Security Posture Management (ASPM)
ASPM is the practice of monitoring and managing an organization’s application security program in response to internal and external signals as an integrated part of the software development lifecycle (SDLC).
Application Security Posture Management (ASPM) is where we transition from leveraging orchestration to centralize and standardize Application Security data to improve scalability and integration of AppSec programs, to transforming this data into actionable information. In DevOps this is the equivalent of moving from monitoring to observability.
ASPM is a framework of processes, technologies and policies designed to provide visibility into the security posture of applications. It helps organizations ensure that applications are secure by monitoring the security state of applications and detecting potential vulnerabilities or threats. It is designed to ensure that the application’s security is aligned with the business risk profile and is closely integrated with the software development lifecycle (SDLC). ASPM also provides an overall assessment of the security posture of an organization’s applications, allowing stakeholders to identify areas for improvement and prioritize application security efforts.
By establishing a baseline of acceptable levels of control in order to detect any deviations from that baseline, ASPM can leverage the data from monitoring activities across all components within an application’s environment, not just vulnerabilities—including code, data, configuration files, external assets such as databases or third-party APIs—ASPM can continually assess the security state against this baseline in order to detect any changes or malicious activity that could compromise the system’s integrity.

From ASOC to ASPM: Evolving from AppSec Monitoring to AppSec Observability
Evolving AppSec Orchestration to AppSec Observability is a critical step in building a secure software development lifecycle (SDLC). While monitoring focuses on automating processes, consolidating and integrating components of an application security program, observability takes it one step further by allowing organizations to monitor and analyze the entire environment to allow them to understand what is important, and what to do about it.
Application Security Posture Management (ASPM) and Application Security Orchestration and Correlation (ASOC) are both important components of an application security program, but they serve different purposes.
- ASOC is the technical backbone that coordinates the policies, processes, and tools involved in the implementation of an end-to-end application security program
- ASPM is the intelligence layer that provides contextual analysis to automate decisions or route information to Development, Security & Operations teams for informed decision making
It is ASPM’s ability to respond to signals – whether self-generated or from external tools – that moves it from orchestration & correlation to posture management. It combines real-time monitoring with insights gathered to provide a holistic view of an organization’s security posture. This allows policies and controls to be enforced throughout the SDLC without human intervention but also allows for exception management where necessary.
By leveraging these components together within an ASPM framework, organizations are able to maintain a consistent level of application security throughout their SDLC process as well as better understand their overall security posture in real-time. This helps reduce risk exposure throughout the entire software development process which ultimately improves customer trust in its products or services while also ensuring compliance with business and industry standards.
ASPM for Risk-Management-by-Design
By implementing risk-management-by-design, an organization recognizes that there is no perfect code., and therefore there cannot be perfect security – and controls for it. This means implementing a series of processes and policies that embody the philosophy “Perfection is the enemy of progress.” (Churchill), balancing all needs of the business: shipping software, ensuring security, generating revenue, etc.
It allows for policies to not be followed, code to be shipped with vulnerabilities, and maybe even breaches to happen – but all set within a risk-accepted framework. This allows Development, Security & Operations to focus their efforts on where they can have the greatest impact in reducing their application security risk. ASPM not only orchestrates and analyzes the requirements implementation and data gathering, but ensures consistency in the execution of a risk-management strategy with:
- Dynamic policy management
- Intelligent Prioritization & Triage
- Automated Security Gatekeeping
- No-Code Workflows Organizations should first establish policies and standards for their applications, which will be used by ASPM to ensure that applications adhere to these standards. This includes defining acceptable risk levels for each application, which can be used as a metric for evaluating the overall security posture of the application, as well as setting up automated controls and processes to enforce the risk framework.

As a continuous process that helps to ensure the security of applications through the use of secure coding practices, automated proactive or reactive scans, and gatekeeping ASPM is also dynamic in nature that can roll out changes automatically to security requirements based on the signals. This ensure code is always ready to ship in line with the most current standards.
Want to learn more about how you can integrate AppSec in your Development pipeline?
Check out these top resources!



Related Articles

Wabbi Named a “Vendor to Watch” in IDC MarketScape: Application Security Posture Management (ASPM) 2025 Vendor Assessment
BOSTON / Press Release / September 18, 2025 Wabbi, a leader in Application Security Posture Management, is proud to announce that it has been named as a Vendor to Watch in the IDC MarketScape: Application Security Posture Management (ASPM) 2025 Vendor Assessment. This...

Tech Deep Dives: DevSecOps Secrets
Click below to listen to this episode of Kabir's Tech Dives, where host Kabir sits down with Brittany Greenfield, founder and CEO of Wabbi, to discuss how Wabbi is revolutionizing application security, the role of cybersecurity in development, and why modern...

Secure by Design: Embedding Risk-Based AppSec in Every Sprint
Secure by Design: Embedding Risk-Based AppSec in Every Sprint In the high-speed development world, embedding security into the software development lifecycle (SDLC) is no longer optional—it’s foundational. But as teams work to shift left and integrate security...

Wabbi Named a “Vendor to Watch” in IDC MarketScape: Application Security Posture Management (ASPM) 2025 Vendor Assessment
BOSTON / Press Release / September 18, 2025 Wabbi, a leader in Application Security Posture Management, is proud to announce that it has been named as a Vendor to Watch in the IDC MarketScape: Application Security Posture Management (ASPM) 2025 Vendor Assessment. This...

How Hackers Use AI Today—And How To Stay Safe – Forbes –
This article originally appeared on Forbes on July 23, 2025 Expert Panel® Forbes Councils Member Forbes Technology Council COUNCIL POST| Membership (Fee-Based) getty As artificial intelligence advances, so do the tactics of malicious actors. Hackers are now...