Navigating the Application Security Posture Management (ASPM) Landscape
The application security market is evolving rapidly, with organizations shifting from fragmented tools to integrated solutions that provide risk-based security management. Understand the challenges of traditional approaches, the advantages of ASPM, and how leading solutions—including Wabbi—are redefining security posture management.

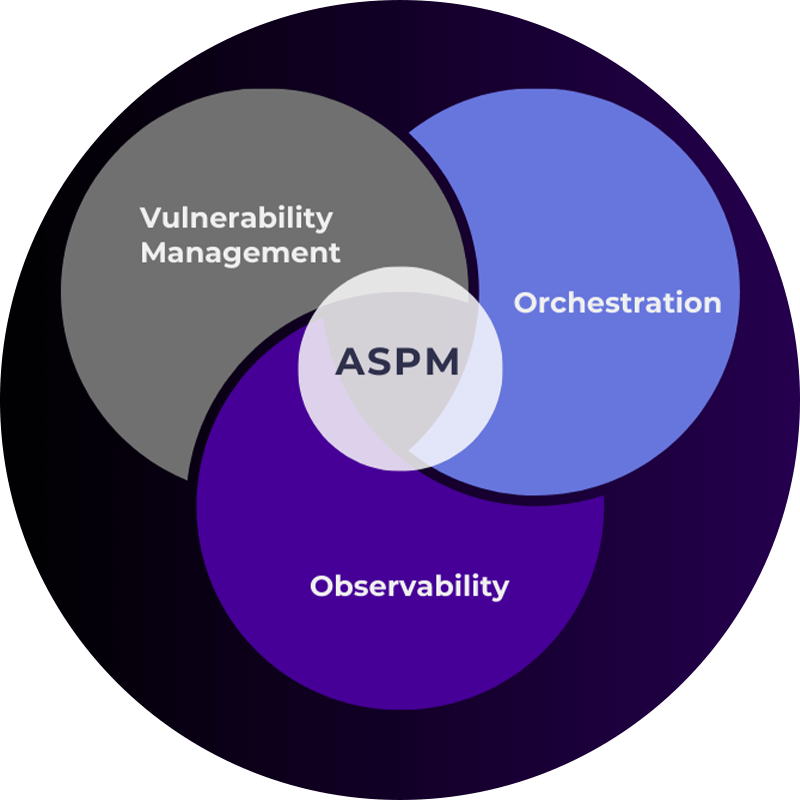
ASPM Uncovered: Piecing Together the Full DevSecOps Puzzle
Understand the full picture of your application security posture. Let us help you organize all the pieces for a comprehensive, long-term ASPM strategy while capturing immediate gains.
Swipe left or right to view the full comparison chart.
| FEATURES | SAMPLE VENDORS | |||||
|---|---|---|---|---|---|---|
 |  |  |  |  |
||
VULNERABILITY MANAGEMENT | Aggregation & Consolidation |  |  |  |  |  |
| App-Specific Risk Based Prioritization |  |  |  |  |
||
| Integrated Backlog Management |  |  |  |  |  |
|
| App Specific Remediation SLA |  |  |  |  |
||
ORCHESTRATION | Policy Deployment |  |  |  |  |
|
| Secure Gatekeeping |  |  |  |
|||
| Workflow Engine |  |  |  |  |
||
| Scheduled Scans |  |  | ||||
OBSERVABILITY | Application Specific Risk Index & Scoring |  |  |  |  |
|
| Guided Actions |  |  |
||||
| Dynamic Management |  |  |  |
|||
| Context-based Alerting |  | |||||
Learn how to Achieve the Promise of DevSecOps
Ready to see how Wabbi can transform your application security strategy? Get started with our comprehensive ASPM platform and achieve the promise of DevSecOps without being overwhelmed.
WHY SETTLE FOR LESS WHEN YOU CAN HAVE IT ALL?
In a world powered by software, application security is everything. At Wabbi, we make deploying security in your SDLC easy and effective.
Wabbi seamlessly translates security policies into development processes, enabling you to achieve Continuous Security and the promise of DevSecOps without compromise.