Team Wabbi
August 14, 2025
Secure by Design: Embedding Risk-Based AppSec in Every Sprint
In the high-speed development world, embedding security into the software development lifecycle (SDLC) is no longer optional—it’s foundational. But as teams work to shift left and integrate security earlier, many fall into the trap of treating all vulnerabilities equally, relying on broad, one-size-fits-all scanning that overloads developers and slows progress.
The real key to modern, effective AppSec? Making it risk-based. That means building security into the sprint—not just as a checklist, but as a strategic function aligned with application risk, business goals, and team workflows.
Here’s how development teams can go from reactive security to secure by design, sprint by sprint.
From Generic Scanning to Risk-Based AppSec
Traditional AppSec practices often emphasize volume: more scans, more findings, more reports. While visibility is important, volume alone doesn’t equate to security. In fact, overloading development teams with hundreds of unprioritized issues can lead to alert fatigue, delayed remediation, and frustrated engineers.
Risk-based AppSec flips the model. Instead of treating every finding the same, it introduces context:
- Is the vulnerability exploitable?
- What data or functionality does it impact?
- What is the business value or criticality of the application it resides in?
- Are there compensating controls in place?
By focusing on the risk, not just the presence of a vulnerability, security becomes a function of prioritization—empowering teams to act on what matters most and defer what doesn’t pose an immediate threat.
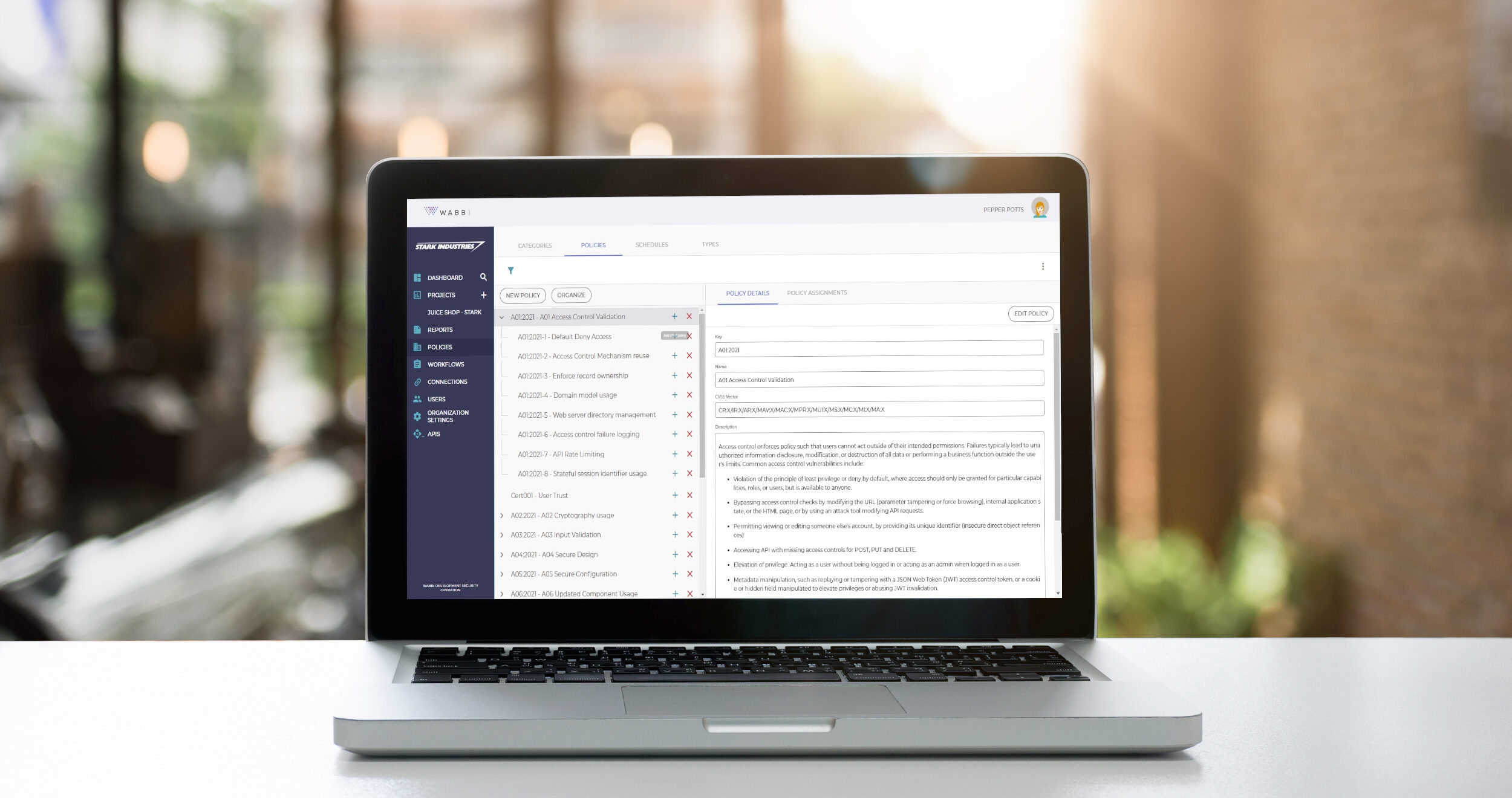
Injecting Risk Evaluation into Sprint Planning
Security isn’t something you “tack on” at the end of a sprint. To be effective and efficient, it needs to be baked into the planning phase—right alongside features and bug fixes.
Here’s how risk-based security evaluation can be included in every sprint planning session:
- Map Security Goals to Business Objectives: Align application security focus with key product outcomes. For example, if a sprint involves a new payment feature, elevate the security rigor accordingly.
- Review Contextual Risk Data: Evaluate existing vulnerabilities not just by severity, but by actual risk. Focus remediation plans on those with the highest exposure or business impact.
- Include Security Tasks in Sprint Backlog: Treat security work like any other development task. Ensure it’s estimated, assigned, and tracked—whether it’s a code fix, a control test, or a dependency upgrade.
- Establish Acceptance Criteria: Define what “secure enough” looks like for each user story, based on risk level. This creates clear guidelines for both dev and QA teams.
- Bring Security to the Table: Include a security representative (or champion) in the sprint planning process to advocate for risk prioritization and answer technical questions.
Enabling Prioritization Through Orchestration
The beauty of risk-based AppSec lies in its ability to drive smart decisions—but that only works when insights are shared, structured, and operationalized across teams.
Orchestration allows organizations to:
- Unify data from various tools (e.g., SAST, DAST, container scanners, third-party assessments) into a single view.
- Normalize and contextualize findings based on application type, user access, production exposure, and other real-world factors.
- Trigger actions (such as ticket creation, policy gating, or remediation guidance) that align with a team’s workflows and risk thresholds.
By prioritizing issues and actions based on risk—not just scan results—teams reduce the noise and focus on closing gaps that actually matter.
Sprint-Level Playbook for Security Champions
Security champions are essential to making AppSec real at the team level. Here’s a simple sprint-by-sprint playbook they can follow to ensure secure-by-design practices:
Sprint Planning
- Review current risk posture for owned applications.
- Identify open risks or vulnerabilities that must be addressed this sprint.
- Help translate security objectives into sprint-ready user stories or tasks.
Sprint Execution
- Facilitate real-time guidance on secure coding practices.
- Coordinate with developers to ensure remediation efforts stay on track.
- Validate that new features follow security guidelines and policies.
Sprint Review
- Highlight resolved vulnerabilities or closed risk gaps.
- Share insights or patterns noticed during development that could impact security posture.
- Reinforce wins and advocate for continued secure-by-design focus.
Sprint Retrospective
- Discuss what went well and what could improve in the AppSec process.
- Refine security criteria or definitions of done based on team feedback.
- Identify areas for better tool integration or process improvement.
Shifting from Secure Eventually to Secure by Design
Security doesn’t have to be a blocker—or an afterthought. By embedding risk-based AppSec into every sprint, teams not only ship code faster but also with greater confidence. It’s about shifting left and shifting smart.
When risk becomes part of the conversation early and often, security evolves from a compliance burden to a true business enabler. And that’s what secure by design is all about: building better software, together, from the very first sprint.
