Brittany Greenfield
May 6, 2024
As the digital landscape continues to evolve at breakneck speed, the importance of integrating security into the Software Development Life Cycle (SDLC) has never been more critical. Today, I’m excited to share with you insights from our latest Annual Continuous Security Report, which uncovered how development and security organizations are tackling the challenge of securing software from its inception to deployment and beyond.
For those unfamiliar with Continuous Security, it goes beyond just the insertion of Sec into DevOps in DevSecOps or even the use of automation and orchestration to enable Security testing to keep pace with Development, but rather looks at the holistic integration of the Application Security Lifecycle into the Software Development lifecycle so that security like software can be managed dynamically in response to the most current needs of the business.


Not surprisingly, recognition that the importance of integration of security into the SDLC is something everybody – literally everybody – agrees is important with 100% reporting it is at least somewhat important, and 61% and 36% saying it is very important or critical, respectively.
And with that recognition, we’ve also seen organizations start to put Continuous Security into action with an impressive 41% of organizations embracing, a significant leap from the mere 12% observed in 2022. This is no surprise as organizations recognize the top benefits to be :
- Ability to foster real-time collaboration between development, operations, and security teams (54%).
- Reducing Security Risk (54%)
- Empowers development teams with the flexibility to manage security within their existing workflows (52%)
The heavy focus on collaboration as a key benefit is no surprise as the cross-functional synergy enabled by Continuous Security enhances communication and coordination, leading to more effective and efficient security practices for Development and Security teams alike.
However, we see a breakdown between the aspirations and the reality as only 32% consistently integrate application security from the start. This gap between understanding and action highlights persisting challenges that hinder effective security integration throughout the SDLC as 94% of organizations acknowledge that their current application security processes are hindering development and delaying time to market, with a substantial 30% reporting significant impediments.
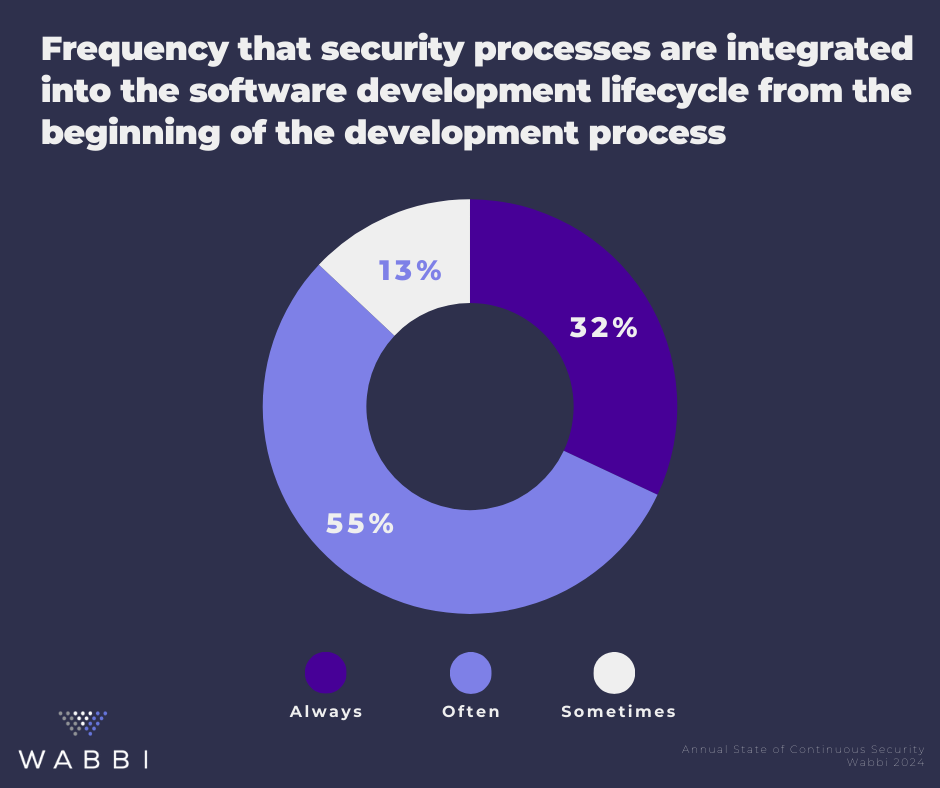
This paradox suggests that while culturally organizations are adopting a Continuous Security mindset, they have failed to implement the technologies that allow them to actually deploy it as part of the SDLC. This disconnect hampers information-sharing and coordination, hindering the ability to address security concerns promptly and efficiently. Consequently, development teams may struggle to ascertain if their code meets the necessary security requirements, leading to potential vulnerabilities and non-compliance issues. Lack of access to accurate and project-specific security policies further exacerbates these challenges. Consequently, we still see 62% of organizations releasing applications with security vulnerabilities.

One lighthouse issue that is apparent from the results is the static nature of application security in their existing implementations, which often remains unchanged despite both security and software being inherently dynamic. This inertia leads to the need for rework, hindering progress and introducing inefficiencies and underscore the need for more robust and adaptable security measures that can accommodate changing demands and provide a clearer understanding of security expectations. Exacerbating these challenges is the lack of automated feedback loops between development and security teams.
While this report continues to highlight the challenges organizations face in breaking down the silos between security and development to fully integrate security in the SDLC and finally realize the promise of DevSecOps, it also underscores the potential of security as an integral part of development strategy, aiming for a future where DevSecOps seamlessly integrates security as the standard practice.
.
We hope you enjoy reading the report and the results as much as the team and I did and would love to hear your thoughts!
You can access all the papers here, read our Press Release here, and join us in conversation on the results on LinkedIn or as I discuss the findings in our upcoming Wabbinar, or our Coffee Chat with CTO Phil Lawrence.
Happy Reading!
Related Articles

16 DevSecOps Trends Shaping The Future Of Software And Cybersecurity – Forbes –
This article originally appeared on Forbes on June 10, 2024 Expert Panel® Forbes Councils Member Forbes Technology Council COUNCIL POST| Membership (Fee-Based) GETTY The ever-evolving field of DevSecOps, which seamlessly integrates security practices into the software...

Total Security Management
Managing Your Application Security Lifecyle in the SDLC The journey to DevOps and CI/CD has been long and arduous for many companies. I know, I’ve been there. And others of you who have been through this understand, it takes a lot to pull all the moving parts...

The Wabbi Wire: Announcing the 2024 State of Continuous Security
In case you didn't hear, Wabbi's Annual State of Continuous Security results are in and we're ready to share the our findings. In this edition of the Wabbi Wire we'll highlight key trends in the industry, discuss insights we discovered on integrating security into...

Wabbi Announces Findings of Annual Continuous Security Report
BOSTON / Press Release / May 6, 2024 Progress in Integrating Security into Software Development, Progress in Adoption, but Bottlenecks Persist Wabbi, the leading application security posture management platform, today announced the findings of its annual report on...
No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.