Let’s Talk About…
Context-Based Vulnerability Management
WHAT ARE WE EXCITED ABOUT IN RELEASE 23.1?
PLATFORM
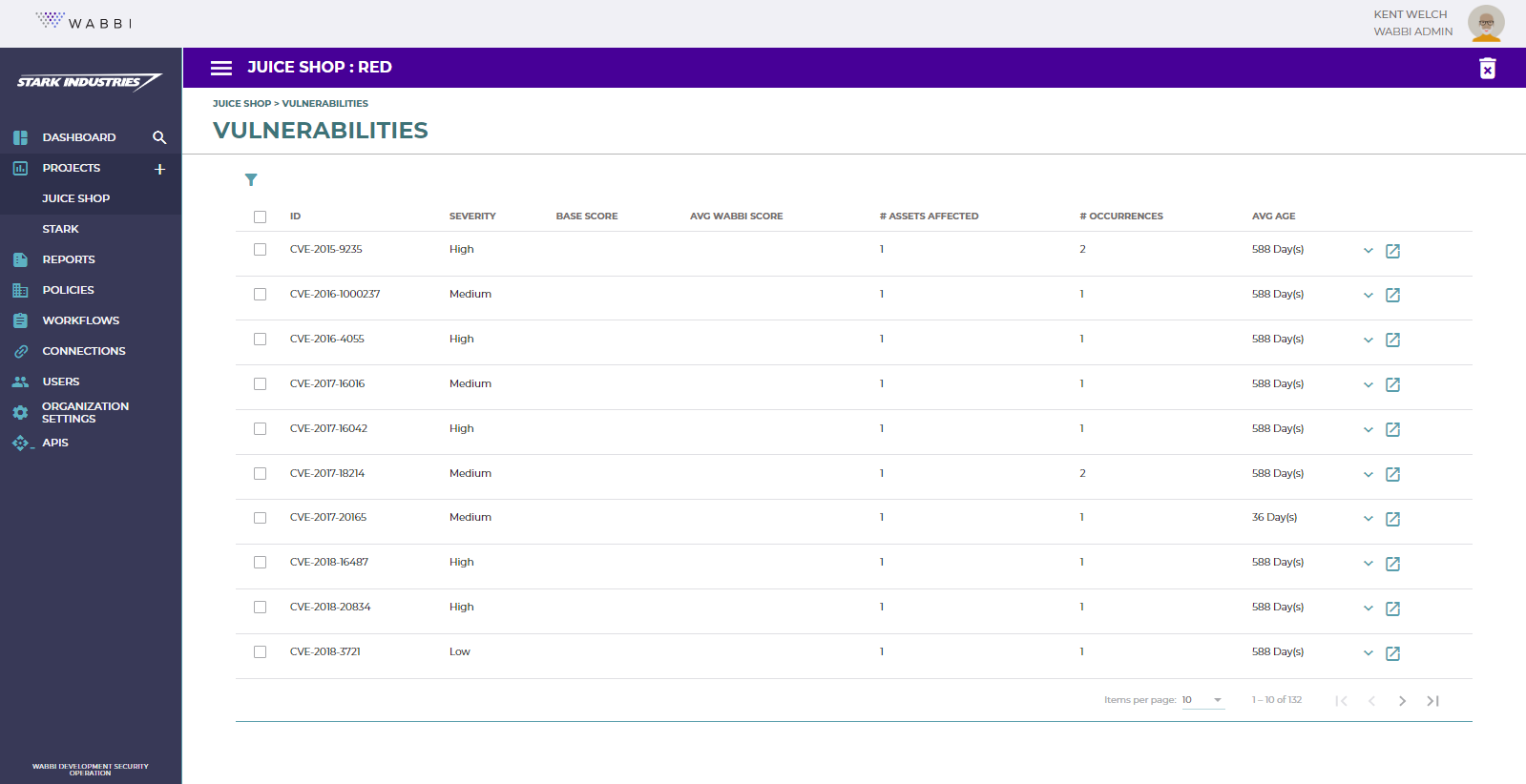
Advanced Vulnerability Table
Expanding upon Wabbi’s core vulnerability management offering, 23.1 introduces a new interface that correlates across the full tool portfolio to analize based on the application specific risk metrics and the ability to grouping by asset to improve analysis capabilities. This provides an easy to navigate, unified view of all vulnerabilities without losing tool-specific information even when different tools describe the vulnerability with different names and provide different remediation guidance.
PLATFORM
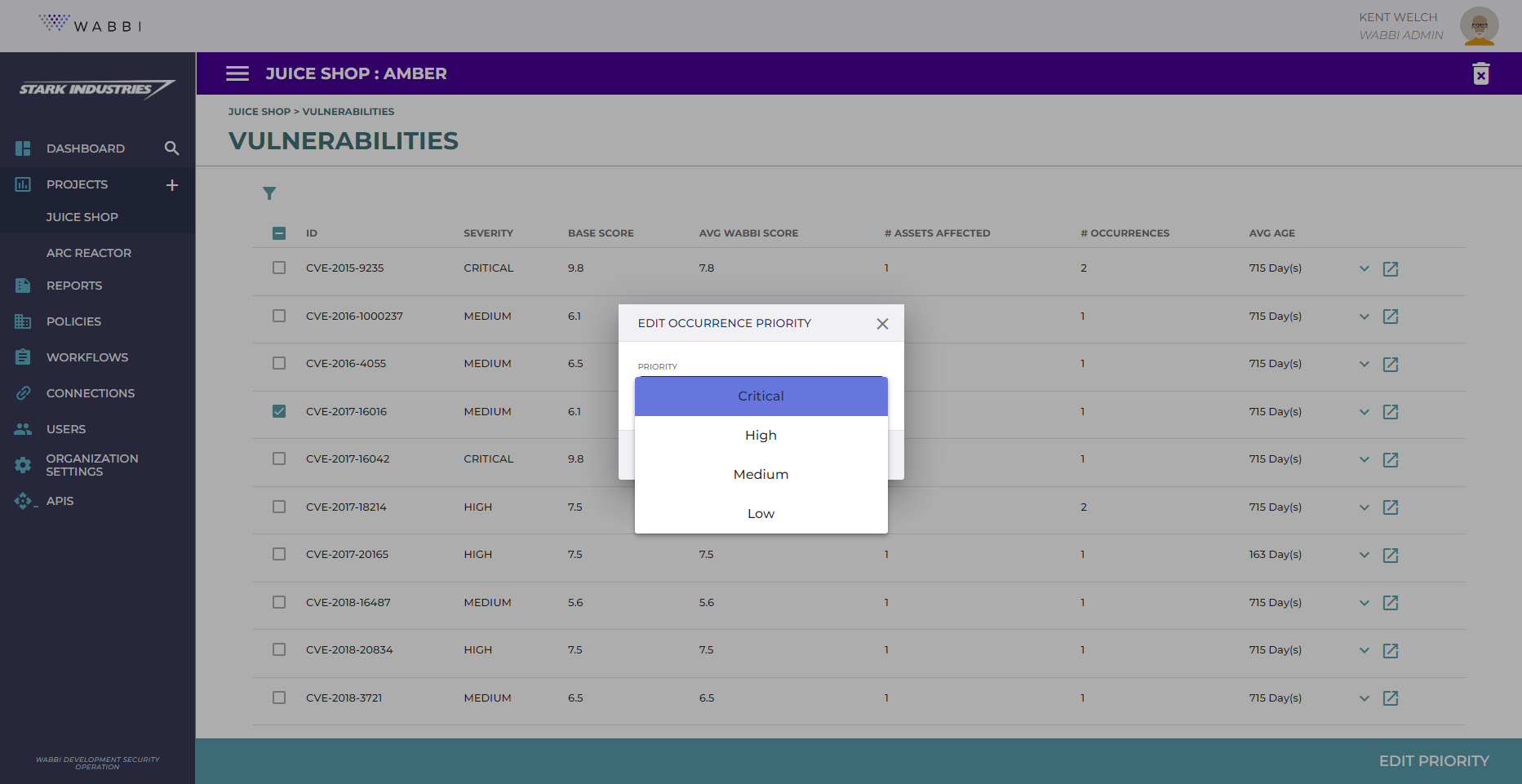
Custom Risk-Based Prioritization
You can’t fix everyhting first: Not all occurrences can be addressed simultaneously, and not all the projects have the same severity. Wabbi’s prioritization engine enables the user to configure the vulnerability priority to differentiate and estimate them, so that teams understand what has to be fixed immediately and what can wait. And with closed loop reporting into ticketing systems, this enables vulnerabilities to be managed from a single backlog without adding noise.
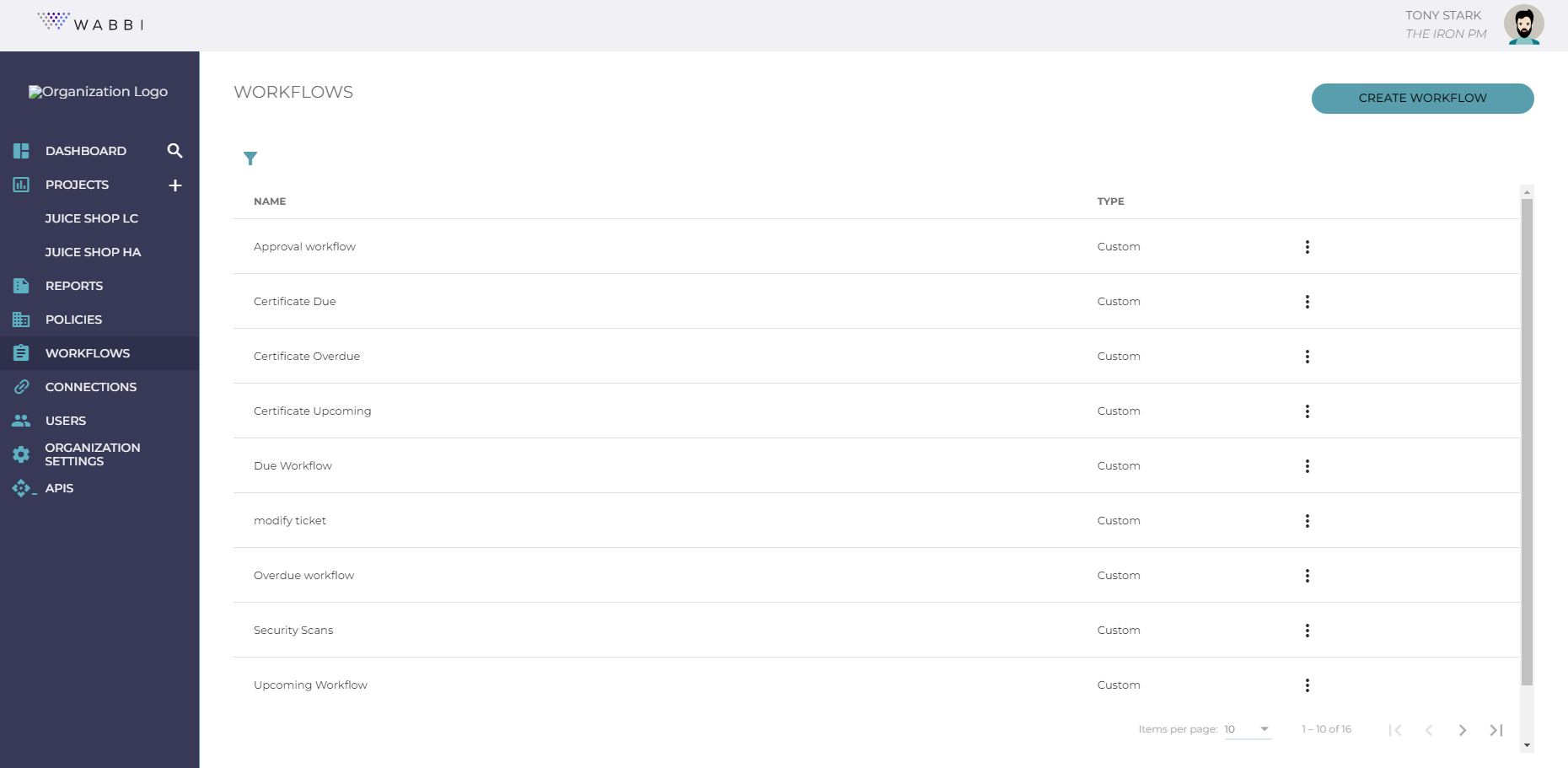
ORCHESTRATION
Security Scan Workflows
Well, you can’t do vulnerability management without, security scans. With 23.1, organizations can standardize their software security testing methodology and workflows from a single location so the right tool is used at the right time without manual intervention. Using Wabbi’s security workflows, you can:
-
Trigger scans from your AppSec tools directly from your CI/CD pipeline
-
Access the results in Wabbi’s Vulnerabilities section
-
Build processes that trigger different actions, such as notifications & ticket creation based on scan results